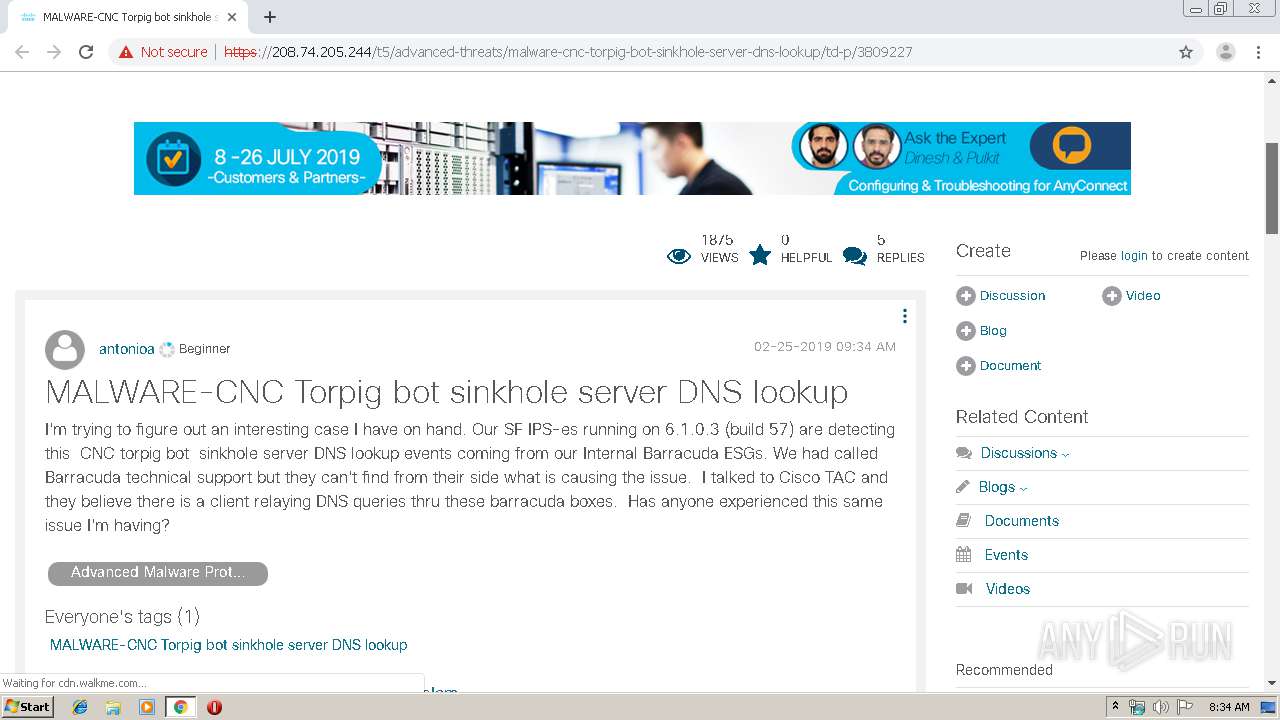
Malware analysis https://208.74.205.244/t5/advanced-threats/malware-cnc-torpig-bot-sinkhole-server-dns-lookup/td-p/3809227 Malicious activity | ANY.RUN - Malware Sandbox Online
Before (left) and after (right) the spread of malware. Check the list... | Download Scientific Diagram






![PDF] CnCHunter: An MITM-approach to identify live CnC servers | Semantic Scholar PDF] CnCHunter: An MITM-approach to identify live CnC servers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a87ce99c3ac3fa1b59afc00272c7b030f982391e/5-Figure4-1.png)
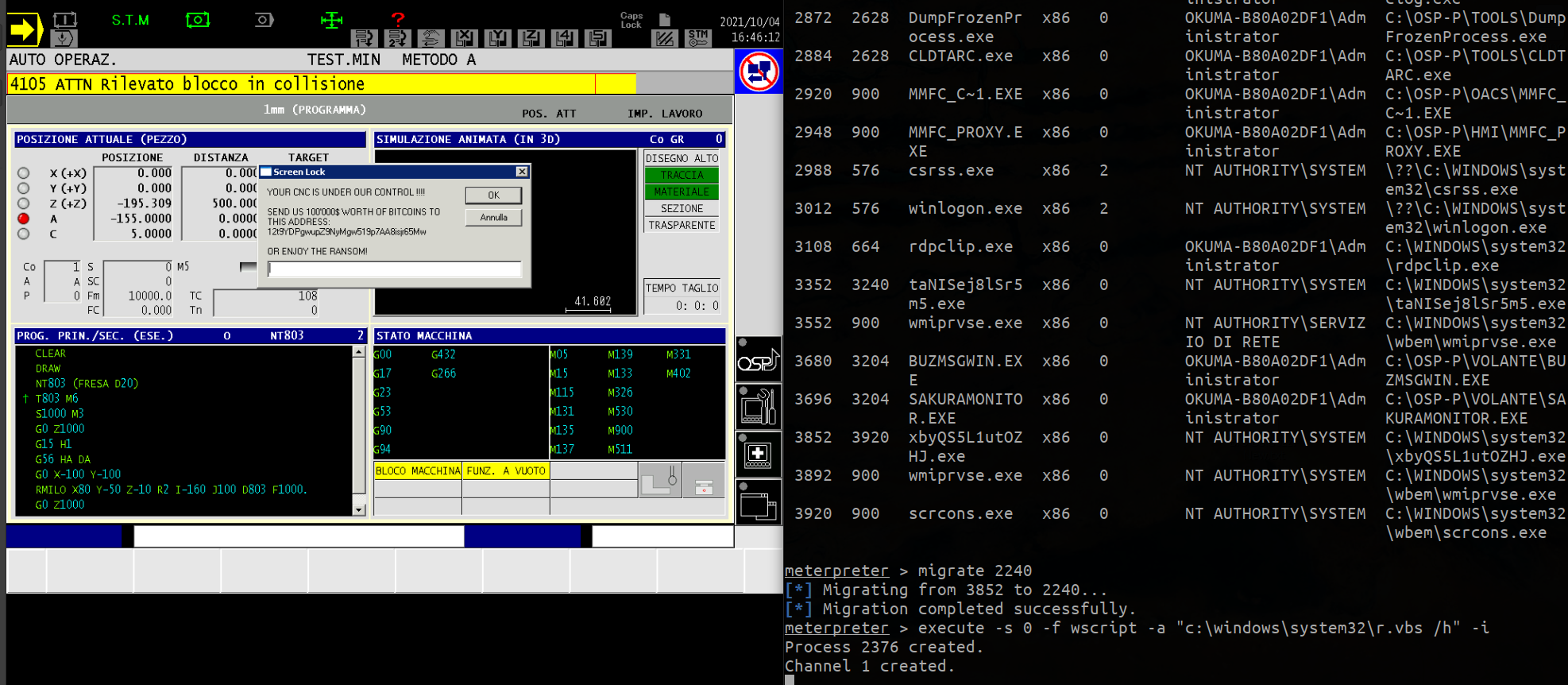





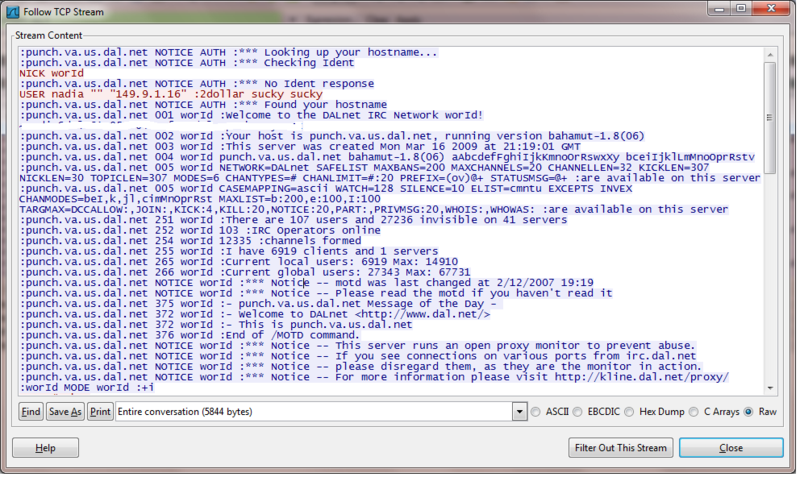
![PDF] CnCHunter: An MITM-approach to identify live CnC servers | Semantic Scholar PDF] CnCHunter: An MITM-approach to identify live CnC servers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a87ce99c3ac3fa1b59afc00272c7b030f982391e/1-Figure1-1.png)

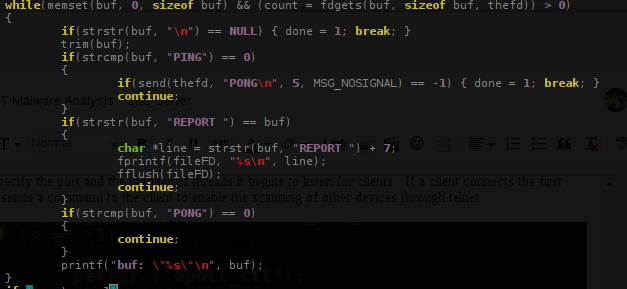

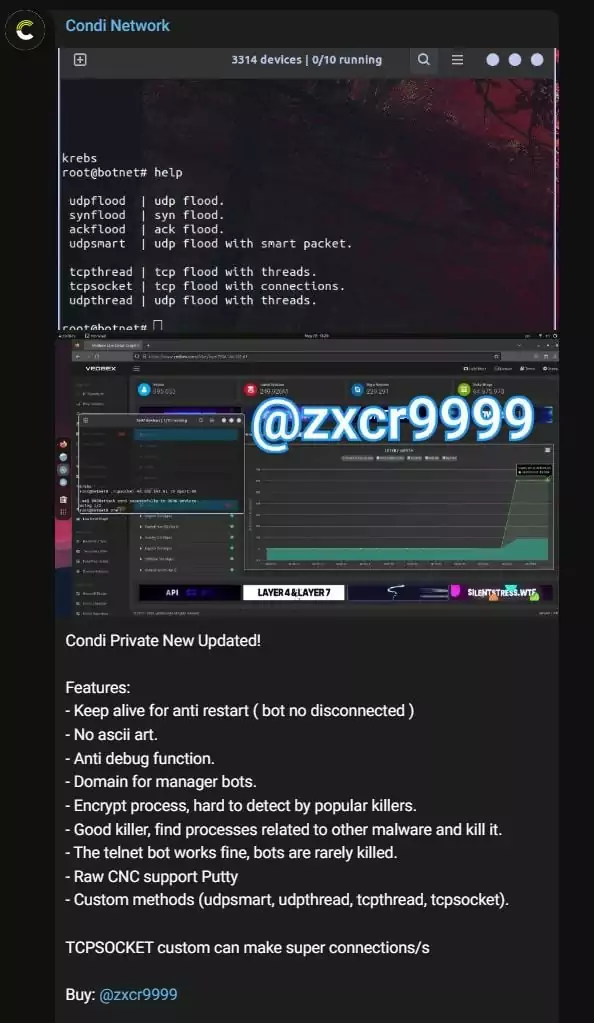
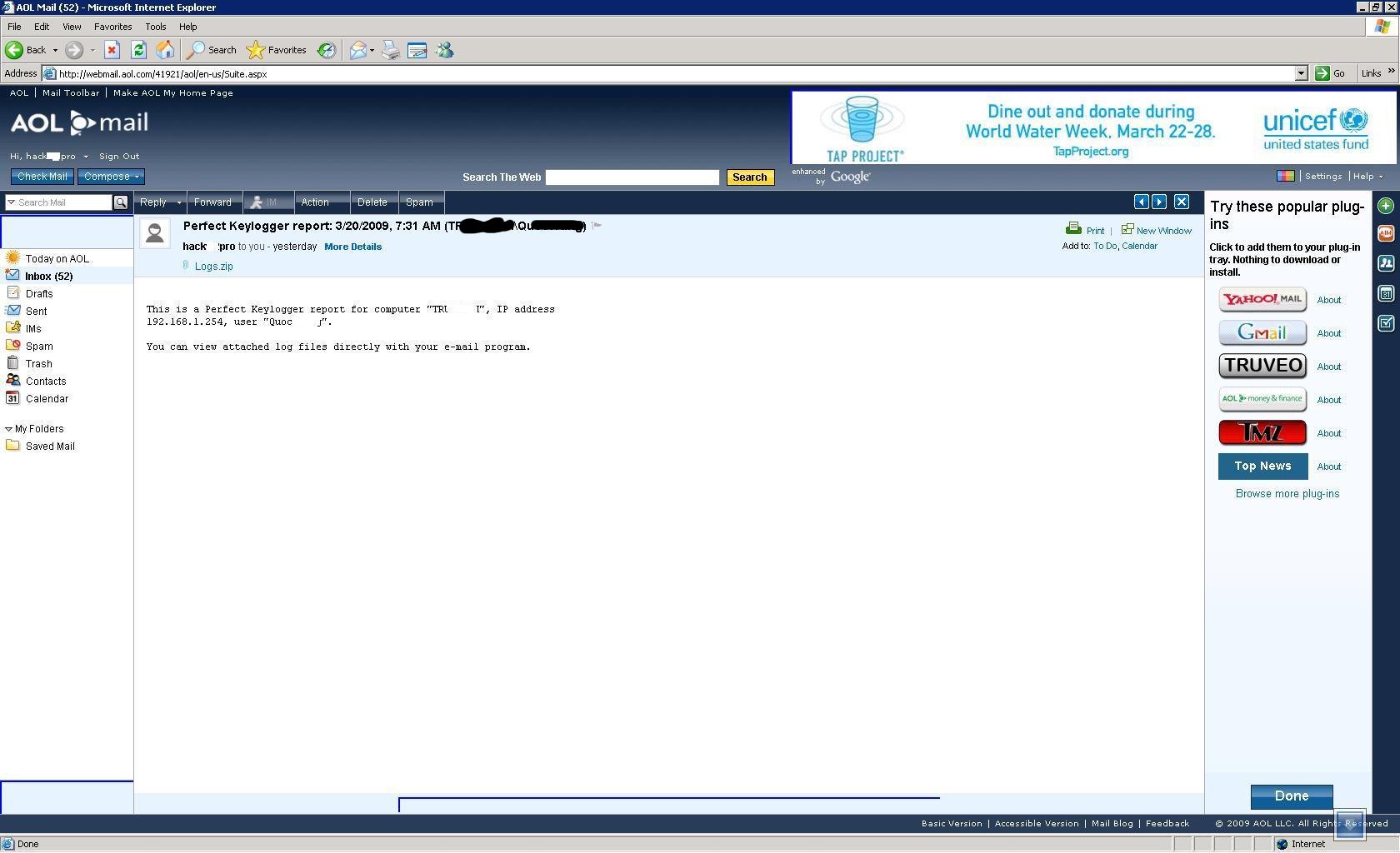
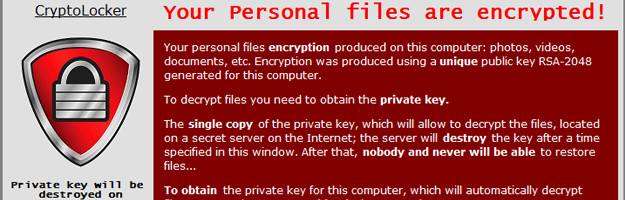

![cnc File ☣ Virus — How to remove & decrypt [cryptoncrypt@tuta.io].cnc? cnc File ☣ Virus — How to remove & decrypt [cryptoncrypt@tuta.io].cnc?](https://howtofix.guide/wp-content/uploads/2021/06/cnc-ransomware.jpg)